Wireshark is a powerful, open-source network protocol analyzer used for capturing and analyzing network traffic. It allows users to inspect network packets in real-time, making it an essential tool for cybersecurity professionals, network administrators, and developers. This blog will guide you on installing Wireshark, using it efficiently, and applying essential filters to analyze network traffic effectively.
📥 Installing Wireshark
Linux (Ubuntu/Debian)
sudo apt update
sudo apt install wireshark -yDuring installation, you might be prompted to allow non-root users to capture packets. Select “Yes” to grant permissions.
Windows
-
Download Wireshark from official website.
-
Run the installer and follow the on-screen instructions.
-
Install Npcap when prompted (necessary for packet capturing).
-
Launch Wireshark and start capturing packets.
🚀 How to Use Wireshark
1️⃣ Start Capturing Packets
-
Open Wireshark.
-
Select the network interface (e.g.,
eth0,wlan0). -
Click Start to begin capturing packets.
2️⃣ Apply Display Filters
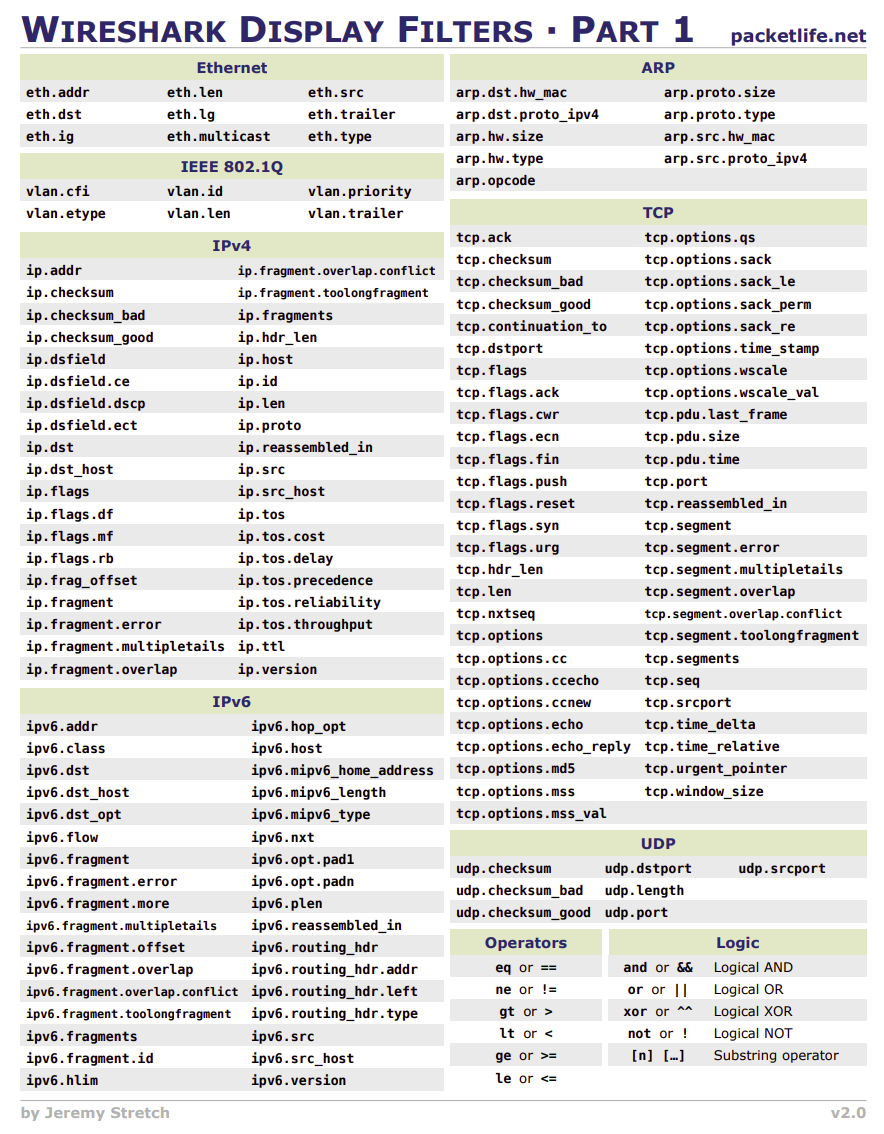
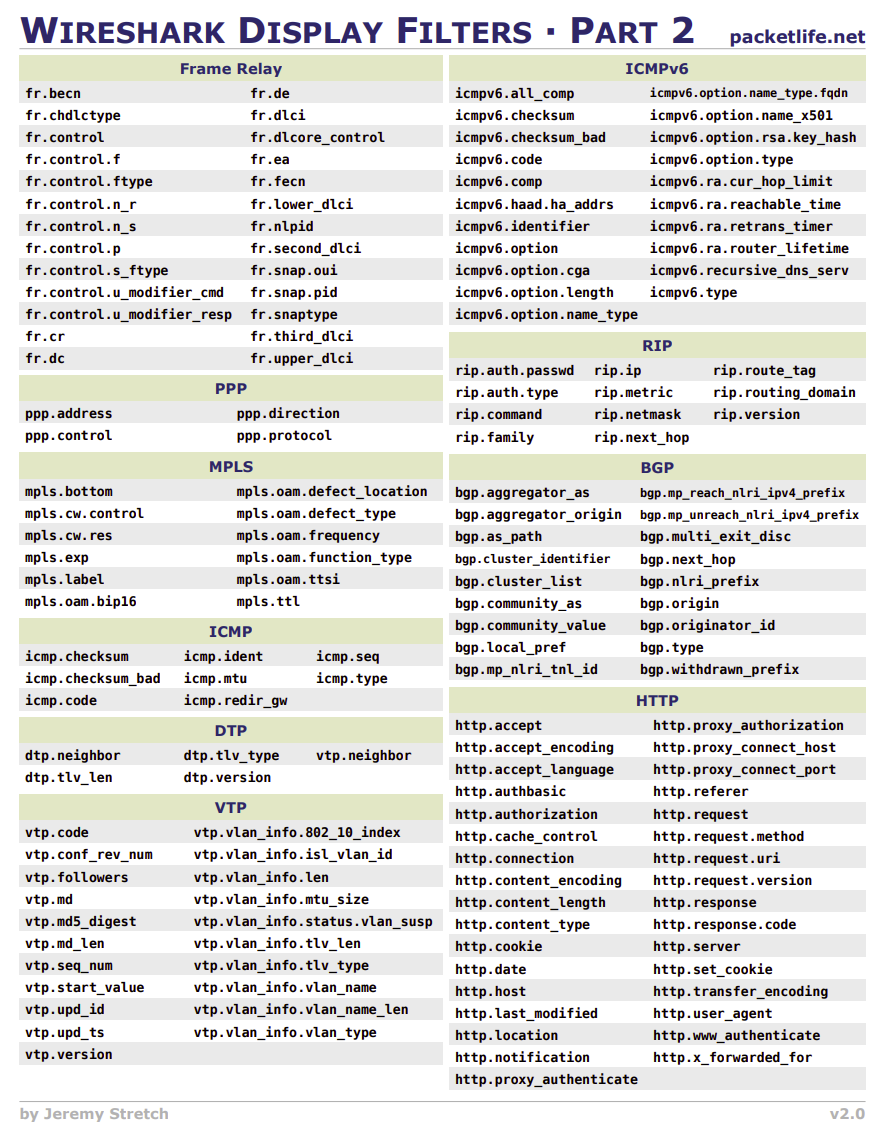
Filters help analyze network traffic efficiently. Some commonly used filters include:
# Filter by IP Address
ip.addr == 10.10.10.9
# Filter by Source or Destination IP
ip.src == 10.10.16.33
ip.dst == 10.10.10.15
# Filter by TCP Port
tcp.port == 25
# Filter by Multiple TCP Ports
ip.addr == 10.10.0.4 or ip.addr == 10.10.0.5
# Filter by IP and Port
ip.addr == 10.10.14.22 and tcp.port == 80803️⃣ Advanced Filtering
# SYN Flag Filter
tcp.flags.syn == 1 and tcp.flags.ack == 0
# Broadcast Traffic Filter
eth.dst == ff:ff:ff:ff:ff:ff
# Filter by Packet Length
ip.dst == 10.0.1.50 && frame.pkt_len > 400
# Filter HTTP GET Requests
http.request
# Filter Packets Containing Specific Word
tcp contains traffic
# Exclude ARP, ICMP, DNS from Capture
!(arp or icmp or dns)Filters Cheat Sheet