Microsoft’s Sysinternals Strings utility is a powerful tool for extracting readable text from binary files, commonly used in reverse engineering, debugging, and security analysis. In this intermediate guide, we’ll explore advanced usage, practical applications, and tips for maximizing its potential.
1. Downloading and Setting Up Strings
-
Download the Utility:
- Visit the Sysinternals Strings Download Page.
- Download the ZIP file and extract
strings.exeto a preferred location.
-
Add to System Path (Optional):
- To run the tool from any directory, add its location to the system PATH:
- Search for “Environment Variables” in Windows.
- Under System Variables, edit the
Pathvariable. - Add the path where
strings.exeis located.
- To run the tool from any directory, add its location to the system PATH:
This configuration lets you execute strings commands from any Command Prompt location.
2. Basic Usage Recap
For a quick reminder, here are the basic commands:
strings.exe <filename>This extracts all readable strings from the specified file.
strings.exe -n <length> <filename>This specifies a minimum length for strings to be extracted.
3. Advanced Options and Techniques
3.1 Filtering Specific Encodings
Strings can extract text in both ASCII and Unicode formats. To specify which to search:
-
ASCII Only:
strings.exe -a <filename>
-
Unicode Only:
strings.exe -u <filename>
3.2 Recursive Directory Scanning
To search all files within a directory and its subdirectories:
strings.exe -s <directory>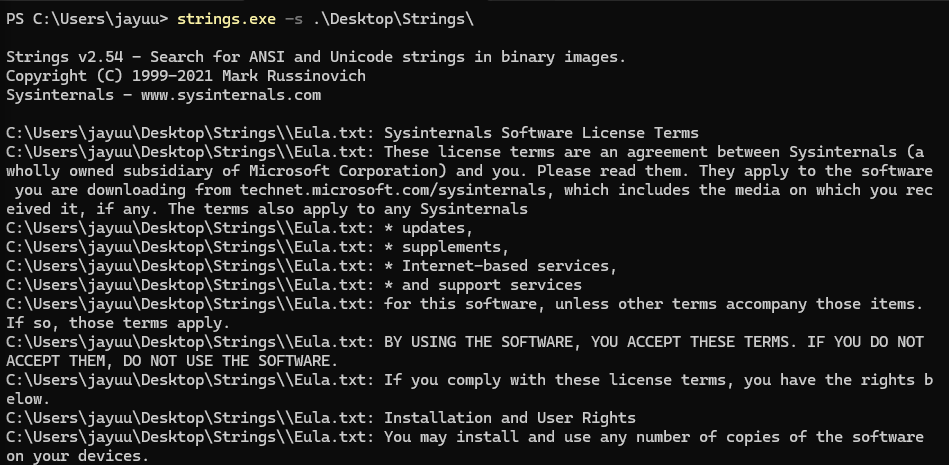
3.3 Outputting Results to a File
Save the output to a text file for detailed analysis:
strings.exe <filename> > output.txt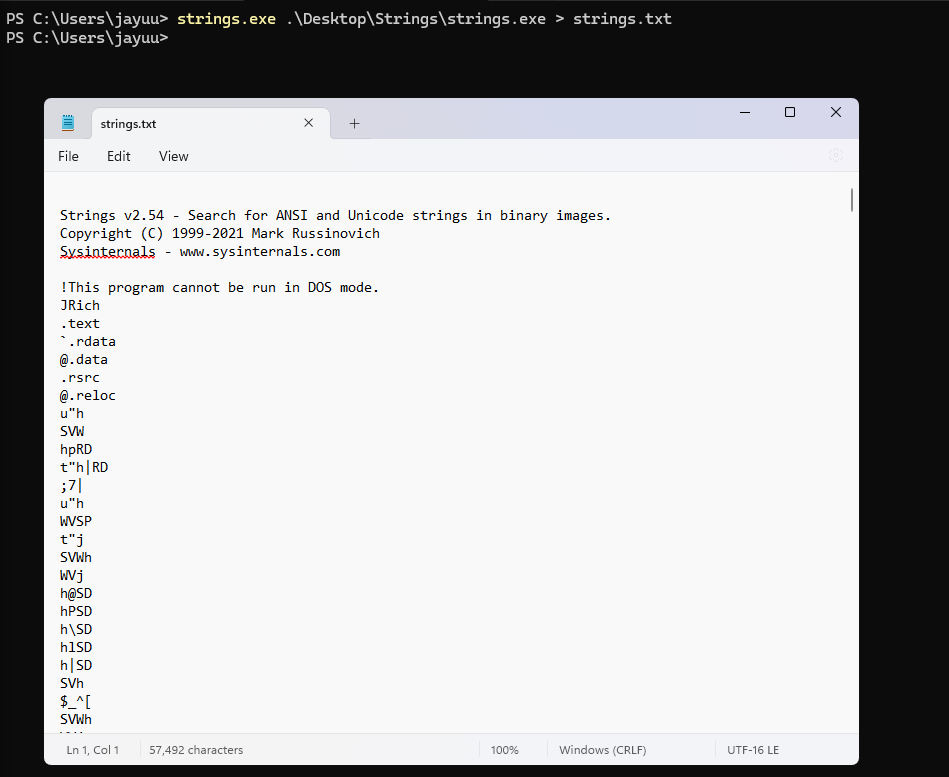
3.4 Piping and Filtering
Combine Strings with other command-line utilities for more refined output. For example, to find URLs in an executable:
strings.exe <filename> | findstr "http https"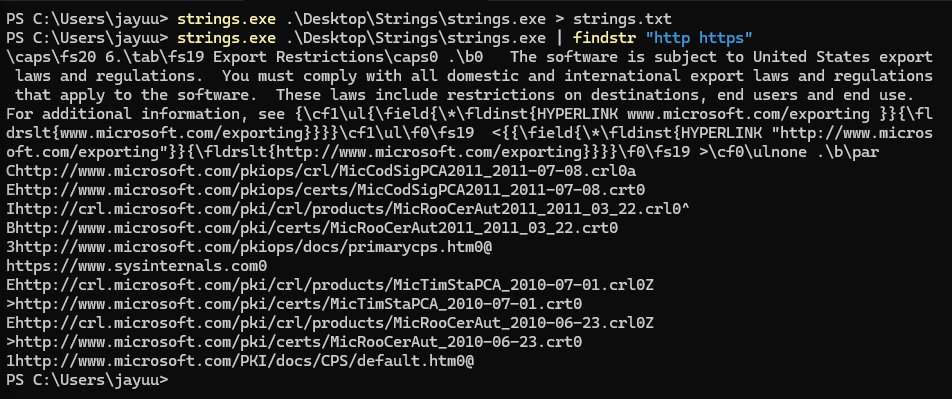
3.5 Combining Multiple Options
Use multiple options together for powerful analysis:
strings.exe -u -n 8 -s <directory> | findstr ".com"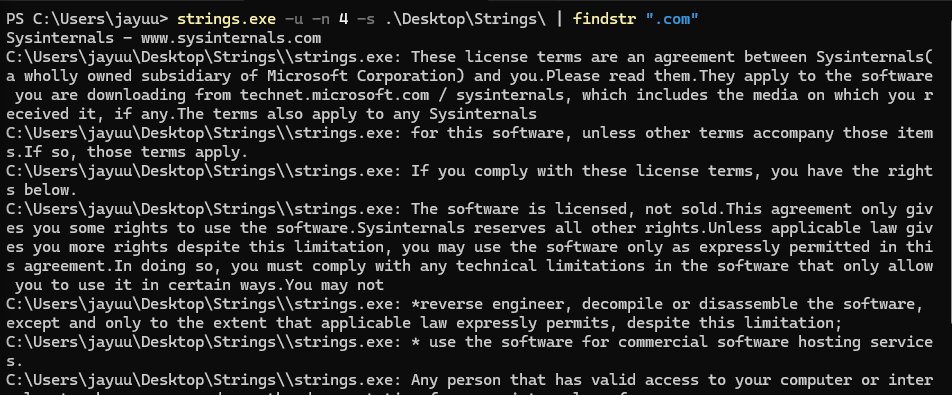
This command searches all subdirectories for Unicode strings with at least 8 characters containing keywords like “.com”.
4. Practical Use Cases
4.1 Malware Analysis
Strings is widely used in malware analysis to extract hardcoded URLs, IP addresses, commands, or even encoded payloads from malicious binaries.
Example:
strings.exe malware.exe | findstr "http https .com .net"4.2 Reverse Engineering and Debugging
Developers and reverse engineers can use Strings to locate error messages, function names, or other identifiers useful for decompiling or debugging software.
Example:
strings.exe -n 5 application.dll | findstr "debug error"4.3 Extracting Metadata
Binary files like images or documents often contain metadata. Strings can help uncover hidden data, comments, or even confidential information unintentionally embedded.
Example:
strings.exe image.jpg | findstr "Author Created Modified"5. Tips and Tricks
-
Combine with PowerShell: Use PowerShell’s
Select-Stringfor even more advanced filtering.strings.exe <filename> | Select-String -Pattern "error|warning" -
Use with Other Sysinternals Tools: Combine Strings with other tools like
ProcmonorAutorunsfor more comprehensive malware analysis or system troubleshooting. -
Regular Expressions: Use regular expressions with
findstrorSelect-Stringto filter complex patterns, such as IP addresses or GUIDs.
6. Example Analysis
Imagine analyzing a suspicious executable named unknown.exe. To extract and examine all readable strings containing URLs or file paths:
strings.exe unknown.exe | findstr /i ".com .net C:\"Sample Output:
https://malicious-site.com
C:\Users\Public\Documents\
This reveals potential C2 (Command and Control) server addresses and file paths used by the executable.
