Running Malware
Running DLL’s
You’ll usually find it simple enough to run executable malware by double-clicking the executable or running the file from the command line, it can be tricky to launch malicious DLLs because Windows doesn’t know how to run them automatically.
The program rundll32.exe is included with all versions of Windows at c:\windows\system32\rundll32.exe
Example :
C:\>rundll32.exe DLLname, Export arguments
C:\>rundll32.exe rip.dll, Install
C:\>rundll32.exe xyzzy.dll, #5Here,
rip.dll is DLLname and Install is a function name or can be ordinal selected from the exported function table in the DLL.
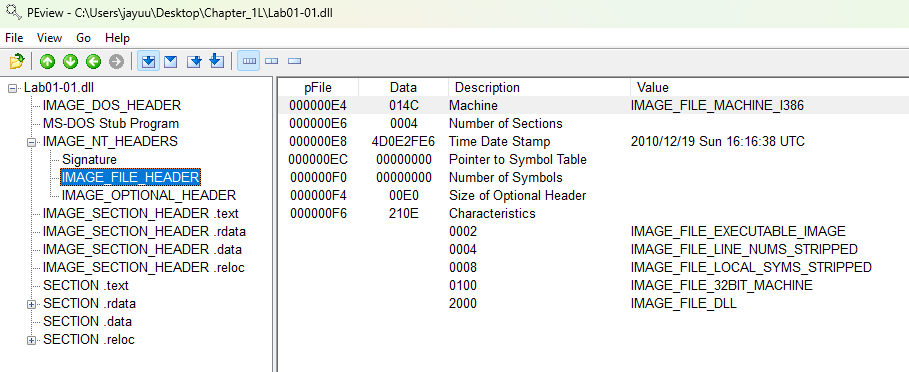
We can use a tool such as PEview or PE Explorer to view the Export table.
Converting DLL to Executable
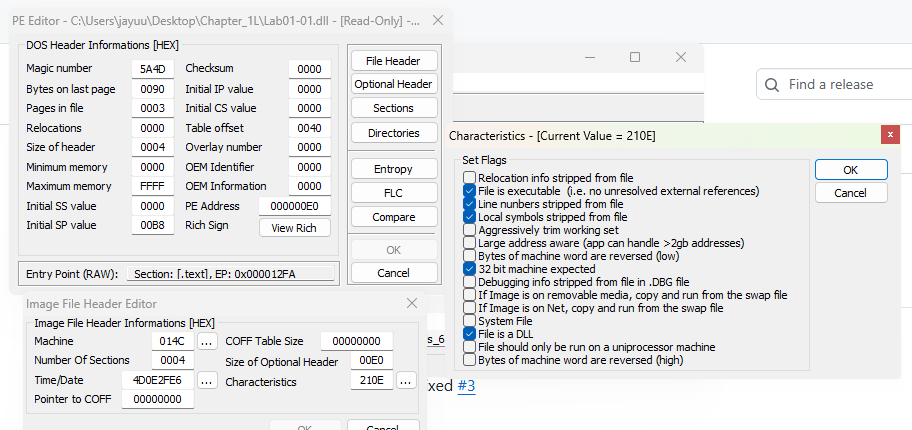
Alternatively, you can even turn a DLL into an executable by modifying the PE header and changing its extension. Wipe the IMAGE_FILE_DLL (0x2000) flag from the Characteristics field in the IMAGE_FILE_HEADER.
To clear the IMAGE_FILE_DLL (0x2000) flag from the Characteristics field in the IMAGE FILE HEADER, you need to modify the Portable Executable (PE) file’s header. To modify the Portable Executable (PE) download PETools and follow below steps.
- Open PETools and Press Alt+1 to select DLL.
- Navigate to File Header → Characteristics’s 3 dots → Unselect File is a DLL → OK.
While this change won’t run any imported functions, it will run the DLLMain method, and it may cause the malware to crash or terminate unexpectedly. However, as long as your changes cause the malware to execute its malicious payload, and you can collect information for your analysis, the rest doesn’t matter.
Installing Service for DLL
DLL malware may also need to be installed as a service, if exports such as InstallService is present.
C:\>rundll32 ipr32x.dll,InstallService ServiceName
C:\>net start ServiceNameMonitoring Malware
Procmon or Process Explorer are an advanced monitoring tools for Windows to Monitor Malware Activity in a system.
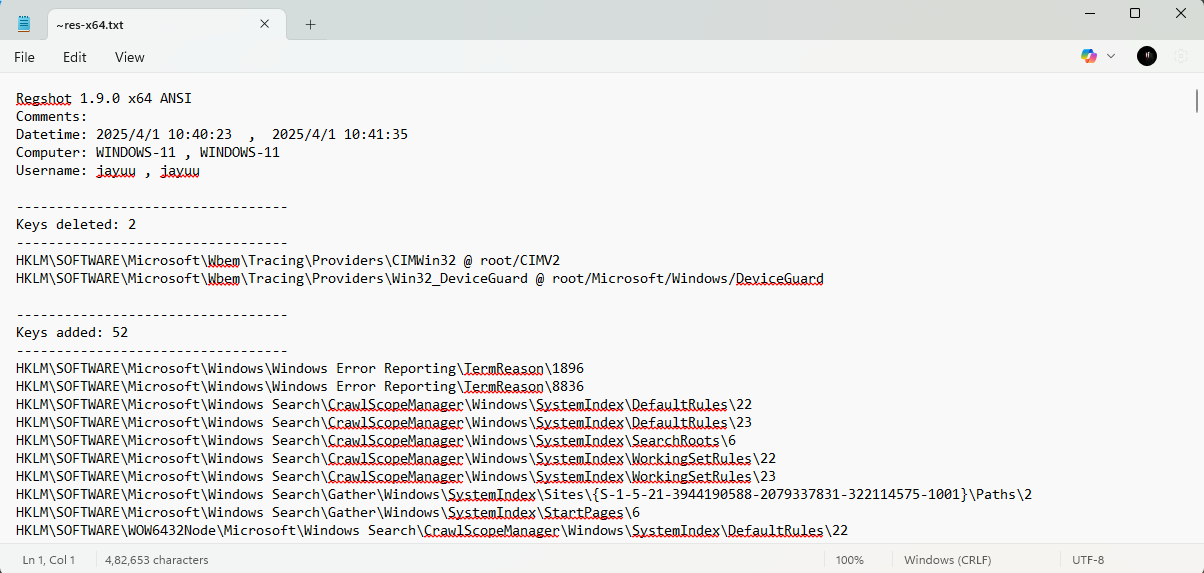
Comparing Registry Snapshots with Regshot
Regshot allows to take and compare two registry snapshots.
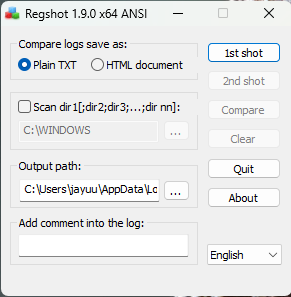
- Simply take the first shot by clicking the 1st Shot button.
- Run the malware and wait for it to finish making any system changes.
- Take the second shot by clicking the 2nd Shot button.
- Finally, click the Compare button to compare the two snapshots.
Faking a Network
Malware often communicates with a command-and-control server. We can create a
fake network to obtain network indicators, without actually connecting to the Internet. These indicators can include DNS names, IP addresses, and packet signatures.
Below are some tools we can use to fake a network.
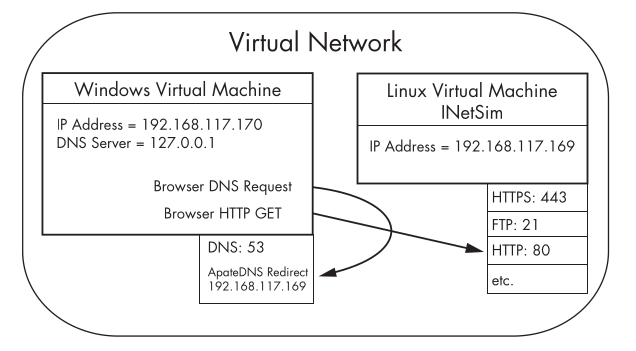
ApateDNS
ApateDNS, capture DNS requests made by malware and spoofs DNS responses to a specified IP address by listening on UDP port 53 on the local machine. ApateDNS can display the hexadecimal and ASCII results of all requests it receives.
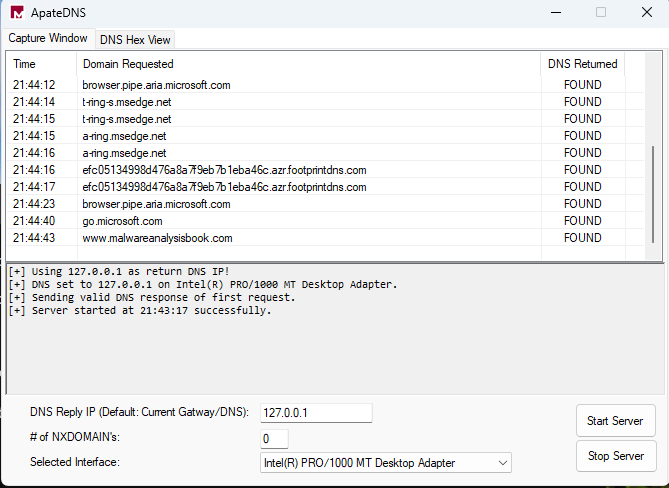
How to use
- Set the IP address of DNS you want.
- Select Interface.
- Click Start Server Button and see requests in Capture Window.
Netcat
Netcat can be used over both inbound and outbound connections for port scanning, tunneling, proxying, port forwarding, and much more. All the data it receives is output to the screen via standard output.
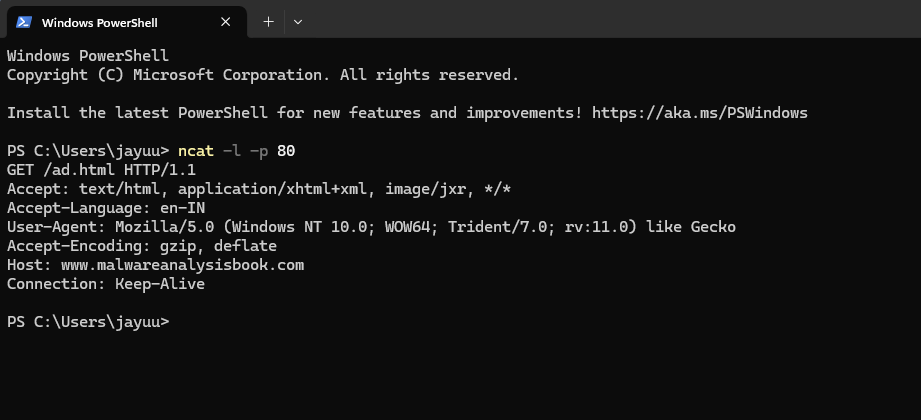
- The –l flag means listen, a–p (with a port number) specifies the port on which to listen.
Packet Sniffing with Wireshark
Wireshark is an open source sniffer, a packet capture tool that intercepts and logs network traffic. Provides visualization, packet-stream analysis, and in-depth analysis of individual packets.
It can be used for both good and evil. It can be used to analyze internal networks and network usage, debug application issues, and study protocols in action. But it can also be used to sniff passwords, reverse-engineer network protocols, steal sensitive information, and listen in on the online chatter at your local coffee shop.
Basic Dynamic Tools in Practice
-
Running procmon and setting a filter on the malware executable name and clearing out all events just before running.
-
Starting Process Explorer.
-
Gathering a first snapshot of the registry using Regshot.
-
Setting up your virtual network to your liking using INetSim and ApateDNS.
-
Setting up network traffic logging using Wireshark.